Get a 10% discount on your first order when you use this promo code at checkout: MAY24BAN3X
7th June Gyamfia Osei #Agent121. Looking for: PICTURE BOOKS, MG, YA, CHILDREN'S NON-FICTION, ADULT FICTION, NON-FICTION
5.0(1)By I Am In Print
LOOKING FOR: ADULT FICTION, NON-FICTION, MG/YA inc GRAPHIC NOVELS Gyamfia Osei has joined Andrew Nurnberg Associates Ltd and is looking for writers of Children's and YA, commercial adult fiction and narrative non-fiction. Gyamfia began her career in publishing working as a Bookseller at Waterstones, before joining Caskie Mushens as a literary assistant in 2018. She relocated to Amsterdam for two years, where she managed international sales for The Pepin Press and held the role of Editor for Plural Magazine, before returning to London in 2021 to start building her own list of authors at The Good Literary Agency. Gyamfia is now an agent at Andrew Nurnberg Associates, representing a diverse list of clients writing children’s books and a bespoke adult list focusing on commercial fiction and narrative non-fiction. Gyamfia is currently looking for contemporary children’s stories that are full of heart and joy-driven books that celebrate kids from underrepresented backgrounds (think Clare Weze, Kimberly Whittam and Elle McNicoll). Unique picture books, funny middle-grade and teen projects (think Angus, Thongs and Perfect Snogging and Glow Up Lara Bloom) are currently at the top of her list this year. She is very interested in finding a graphic novel or illustrated project for either MG or YA readers. She is very open when it comes to Children’s non-fiction but would be particularly interested to consider unique cookbooks aimed at young chefs, books exploring mental health/wellness and projects that bring the experiences of marginalised children to the forefront. In the adult fiction space, Gyamfia enjoys well-plotted, fast-paced narratives with authentic characters who lodge themselves in her mind long after she’s finished reading (think Big Little Lies, Verity and Girl A). She’s open to a broad range of genres, but would be particularly keen to see cosy crime, global stories and tightly plotted domestic noir. In the adult non-fiction space, she would be happy to consider commercial narrative non-fiction and cultural history projects (think Brit(ish), It’s Not That Radical and Everything I Know About Love). Gyamfia would like you to submit a covering letter, 1 page synopsis and the opening three chapters (max 5,000 words). For picture books please send two texts and a covering letter. For non-fiction please supply a cover letter and proposal with up to 5,000 words of your sample text. (In addition to the paid sessions, Gyamfia is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk [agent121@iaminprint.co.uk] to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Tuesday 4 June 2024

PORTRAYING REALISTIC RELATIONSHIPS IN PERFORMANCE
By Fay Beck Studio
AN ONLINE ACTING COURSE ON HOW TO PORTRAY REALISTIC RELATIONSHIPS ON SCREEN AND STAGE Stories are always about people in relationships. Werther they involve real human beings, inanimate objects or ideas, characters in film and theatre are either motivated or hindered by people and things they have some kind of relationship with. Skilled actors are able to ’embody’ relationships convincingly and genuinely. Their interactions with their co-stars are richly layered and nuanced – much like our relationships are in real life. ‘What’, they do and ‘how’, they do things with each other reveals specificity in the relationships they are depicting. This specificity is so important in performance that sometimes it may be a major reason why a particular actor is chosen for a certain part. As an audience member you may have experienced how powerful relationships work is. You many have found yourself walking away from a performance, saying that the lead actors had ‘chemistry’ with each other – or, that they did not. Despite how key relationships work is, actors are rarely taught how to do it exclusively. As a result, actors feel uncertain about how to properly ‘get into’ or embody a particular relationship. This course has been designed for exactly this purpose! TRAINING ESPECIALLY TO DO RELATIONSHIP WORK Part theory, part practice, the course will introduce you to practical tools you can use right now to elevate your auditions and acting performances. The first part of the course focuses on equipping you with tools you need to recognise relationships in script work. The second part of the course is purely practical. Through a set of exercises you’ll learn how to embody different relationships convincingly. Or said differently, how to be truthfully ‘in them’ during your performance. COURSE REQUIREMENTS * INTERMEDIATE ACTORS WELCOME: To join the course you will need at least intermediate acting skills. Good script analysis skills are presumed. * BEGINNING ACTORS: Consider doing the Script Analysis Course. You will benefit much more from this course if you are well equipped with sound script analysis skills. * EXPERIENCED ACTORS: This course is recommend for you! Elevate existing acting skills KEY POINTS * 5 WEEK COURSE, 5 X 2HR WEEKLY CLASS (TOTAL 10HRS) * SMALL GROUP (MAX 10 PEOPLE) TO POWER LEARNING * SESSIONS CONDUCTED LIVE OVER GOOGLE MEET * CLASSES AVAILABLE TO WATCH BACK WHILE THE COURSE IS RUNNING * 50% THEORY, 50% PRACTICE/HOMEWORK PLAYBACK Desire and training bring you to the precipice of success. Then you still have a mountain to climb. FAY BECK LEARNING OUTCOMES * Understanding how Relationships 'shift' meaning and story * Recognising Relationships in text * Creating personal connection to text through Relationships work * Learned how to craft Relationships with people * Learned how to craft Relationships with in-animate objects, animals and ideas * Practiced Substitution Exercises COURSE TERMS MAY 25TH – JUNE 22ND 2024 5 Consecutive SATURDAYS Join us from any timezone around the world. The course runs at generally convenient times for the following Timezones: Universal Time Coordinated (UTC): 09:00 AM – 11:00 AM Greenwhich Mean Time (GMT): 10:00 AM – 12:00 PM (EG. LONDON, GB) Central European Time (CET): 11:00 AM – 13:00 PM (EG, BERLIN, PARIS, ROME) (UTC+4): 13:00 PM – 15:00 PM (EG, DUBAI) Australian Western Standard Time (AWST) 17:00 PM – 19:00 PM (EG. PERTH) Australian Central Standard Time (ACST) 18:30 PM – 20:30 PM (EG. ADELAIDE) Australian Eastern Standard Time (AEST) 19:00 PM – 21:00 PM (EG. Brisbane, Sydney, Melbourne) Not a convenient time for you? Don’t worry this course will run again at a time more suitable for your timezone. Keep up with upcoming by signing up to our newsletter!

Sculpt a Character from the Post Apocalypse
By Course Cloud
COURSE OVERVIEW Learn how to use the most advanced 3D sculpting software to create a fully-formed futuristic figure with this course on how to Sculpt a Character from the Post Apocalypse. Make use of Zbrush and its most flexible functions to build a denizen from a dark reality and realise its features in the most professional way possible. By taking this Character Sculpting tuition, you will quickly learn the visual skills and programming knowledge you'll need to turn a flat image into a 3D road warrior. You will be guided through the techniques needed to fully realise your figure in their digital universe. By sculpting this character and producing an appealing final model, you will learn how to create other characters in the same way. This best selling Sculpt a Character from the Post Apocalypse has been developed by industry professionals and has already been completed by hundreds of satisfied students. This in-depth Sculpt a Character from the Post Apocalypse is suitable for anyone who wants to build their professional skill set and improve their expert knowledge. The Sculpt a Character from the Post Apocalypse is CPD-accredited, so you can be confident you're completing a quality training course will boost your CV and enhance your career potential. The Sculpt a Character from the Post Apocalypse is made up of several information-packed modules which break down each topic into bite-sized chunks to ensure you understand and retain everything you learn. After successfully completing the Sculpt a Character from the Post Apocalypse, you will be awarded a certificate of completion as proof of your new skills. If you are looking to pursue a new career and want to build your professional skills to excel in your chosen field, the certificate of completion from the Sculpt a Character from the Post Apocalypse will help you stand out from the crowd. You can also validate your certification on our website. We know that you are busy and that time is precious, so we have designed the Sculpt a Character from the Post Apocalypse to be completed at your own pace, whether that's part-time or full-time. Get full course access upon registration and access the course materials from anywhere in the world, at any time, from any internet-enabled device. Our experienced tutors are here to support you through the entire learning process and answer any queries you may have via email.

EC-Council Computer Hacking Forensic Investigator (CHFI) v10.0
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The CHFI course will benefit: Police and other laws enforcement personnel Defense and Military personnel e-Business Security professionals Systems administrators Legal professionals Banking, Insurance and other professionals Government agencies Overview At the end of this course, you will possess the skills needed to: Understand the fundamentals of computer forensics Understand the computer forensic investigation process Describe in detail different types of hard disks and file systems Understand data acquisition and duplication Counteract anti-forensic techniques Leverage forensic skills in Windows, Linux, and Mac Investigate web attacks Understand dark web forensics Deploy forensic techniques for databases, cloud, and networks Investigate email crimes including malware Perform forensics in mobile and IoT environments Every crime leaves a digital footprint, and you need the skills to track those footprints. In this course, students will learn to unravel these pieces of evidence, decode them and report them. From decoding a hack to taking legal action against the perpetrators, they will become an active respondent in times of cyber-breaches. COMPUTER FORENSICS IN TODAY?S WORLD * 1.1. Understand the Fundamentals of Computer Forensics * 1.2. Understand Cybercrimes and their Investigation Procedures * 1.3. Understand Digital Evidence * 1.4. Understand Forensic Readiness, Incident Response and the Role of SOC (Security * Operations Center) in Computer Forensics * 1.5. Identify the Roles and Responsibilities of a Forensic Investigator * 1.6. Understand the Challenges Faced in Investigating Cybercrimes * 1.7. Understand Legal Compliance in Computer Forensics * COMPUTER FORENSICS INVESTIGATION PROCESS * 2.1. Understand the Forensic Investigation Process and its Importance * 2.2. Understand the Pre-investigation Phase * 2.3. Understand First Response * 2.4. Understand the Investigation Phase * 2.5. Understand the Post-investigation Phase * UNDERSTANDING HARD DISKS AND FILE SYSTEMS * 3.1. Describe Different Types of Disk Drives and their Characteristics * 3.2. Explain the Logical Structure of a Disk * 3.3. Understand Booting Process of Windows, Linux and Mac Operating Systems * 3.4. Understand Various File Systems of Windows, Linux and Mac Operating Systems * 3.5. Examine File System Using Autopsy and The Sleuth Kit Tools * 3.6 Understand Storage Systems * 3.7. Understand Encoding Standards and Hex Editors * 3.8. Analyze Popular File Formats Using Hex Editor * DATA ACQUISITION AND DUPLICATION * 4.1. Understand Data Acquisition Fundamentals * 4.2. Understand Data Acquisition Methodology * 4.3. Prepare an Image File for Examination * DEFEATING ANTI-FORENSICS TECHNIQUES * 5.1. Understand Anti-forensics Techniques * 5.2. Discuss Data Deletion and Recycle Bin Forensics * 5.3. Illustrate File Carving Techniques and Ways to Recover Evidence from Deleted Partitions * 5.4. Explore Password Cracking/Bypassing Techniques * 5.5. Detect Steganography, Hidden Data in File System Structures, Trail Obfuscation, and File Extension Mismatch * 5.6. Understand Techniques of Artifact Wiping, Overwritten Data/Metadata Detection, and Encryption * 5.7. Detect Program Packers and Footprint Minimizing Techniques * 5.8. Understand Anti-forensics Countermeasures * WINDOWS FORENSICS * 6.1. Collect Volatile and Non-volatile Information * 6.2. Perform Windows Memory and Registry Analysis * 6.3. Examine the Cache, Cookie and History Recorded in Web Browsers * 6.4. Examine Windows Files and Metadata * 6.5. Understand ShellBags, LNK Files, and Jump Lists * 6.6. Understand Text-based Logs and Windows Event Logs * LINUX AND MAC FORENSICS * 7.1. Understand Volatile and Non-volatile Data in Linux * 7.2. Analyze Filesystem Images Using The Sleuth Kit * 7.3. Demonstrate Memory Forensics Using Volatility & PhotoRec * 7.4. Understand Mac Forensics * * NETWORK FORENSICS * 8.1. Understand Network Forensics * 8.2. Explain Logging Fundamentals and Network Forensic Readiness * 8.3. Summarize Event Correlation Concepts * 8.4. Identify Indicators of Compromise (IoCs) from Network Logs * 8.5. Investigate Network Traffic * 8.6. Perform Incident Detection and Examination with SIEM Tools * 8.7. Monitor and Detect Wireless Network Attacks * INVESTIGATING WEB ATTACKS * 9.1. Understand Web Application Forensics * 9.2. Understand Internet Information Services (IIS) Logs * 9.3. Understand Apache Web Server Logs * 9.4. Understand the Functionality of Intrusion Detection System (IDS) * 9.5. Understand the Functionality of Web Application Firewall (WAF) * 9.6. Investigate Web Attacks on Windows-based Servers * 9.7. Detect and Investigate Various Attacks on Web Applications * DARK WEB FORENSICS * 10.1. Understand the Dark Web * 10.2. Determine How to Identify the Traces of Tor Browser during Investigation * 10.3. Perform Tor Browser Forensics * DATABASE FORENSICS * 11.1. Understand Database Forensics and its Importance * 11.2. Determine Data Storage and Database Evidence Repositories in MSSQL Server * 11.3. Collect Evidence Files on MSSQL Server * 11.4. Perform MSSQL Forensics * 11.5. Understand Internal Architecture of MySQL and Structure of Data Directory * 11.6. Understand Information Schema and List MySQL Utilities for Performing Forensic Analysis * 11.7. Perform MySQL Forensics on WordPress Web Application Database * CLOUD FORENSICS * 12.1. Understand the Basic Cloud Computing Concepts * 12.2. Understand Cloud Forensics * 12.3. Understand the Fundamentals of Amazon Web Services (AWS) * 12.4. Determine How to Investigate Security Incidents in AWS * 12.5. Understand the Fundamentals of Microsoft Azure * 12.6. Determine How to Investigate Security Incidents in Azure * 12.7. Understand Forensic Methodologies for Containers and Microservices * INVESTIGATING EMAIL CRIMES * 13.1. Understand Email Basics * 13.2. Understand Email Crime Investigation and its Steps * 13.3. U.S. Laws Against Email Crime * MALWARE FORENSICS * 14.1. Define Malware and Identify the Common Techniques Attackers Use to Spread Malware * 14.2. Understand Malware Forensics Fundamentals and Recognize Types of Malware Analysis * 14.3. Understand and Perform Static Analysis of Malware * 14.4. Analyze Suspicious Word and PDF Documents * 14.5. Understand Dynamic Malware Analysis Fundamentals and Approaches * 14.6. Analyze Malware Behavior on System Properties in Real-time * 14.7. Analyze Malware Behavior on Network in Real-time * 14.8. Describe Fileless Malware Attacks and How they Happen * 14.9. Perform Fileless Malware Analysis - Emotet * MOBILE FORENSICS * 15.1. Understand the Importance of Mobile Device Forensics * 15.2. Illustrate Architectural Layers and Boot Processes of Android and iOS Devices * 15.3. Explain the Steps Involved in Mobile Forensics Process * 15.4. Investigate Cellular Network Data * 15.5. Understand SIM File System and its Data Acquisition Method * 15.6. Illustrate Phone Locks and Discuss Rooting of Android and Jailbreaking of iOS Devices * 15.7. Perform Logical Acquisition on Android and iOS Devices * 15.8. Perform Physical Acquisition on Android and iOS Devices * 15.9. Discuss Mobile Forensics Challenges and Prepare Investigation Report * IOT FORENSICS * 16.1. Understand IoT and IoT Security Problems * 16.2. Recognize Different Types of IoT Threats * 16.3. Understand IoT Forensics * 16.4. Perform Forensics on IoT Devices *

CompTIA Data+
By Nexus Human
Duration 5 Days 30 CPD hours Overview Mining data Manipulating data Visualizing and reporting data Applying basic statistical methods Analyzing complex datasets while adhering to governance and quality standards throughout the entire data life cycle CompTIA Data+ is an early-career data analytics certification for professionals tasked with developing and promoting data-driven business decision-making. CompTIA Data+ gives you the confidence to bring data analysis to life. As the importance for data analytics grows, more job roles are required to set context and better communicate vital business intelligence. Collecting, analyzing, and reporting on data can drive priorities and lead business decision-making. 1 - IDENTIFYING BASIC CONCEPTS OF DATA SCHEMAS * Identify Relational and Non-Relational Databases * Understand the Way We Use Tables, Primary Keys, and Normalization 2 - UNDERSTANDING DIFFERENT DATA SYSTEMS * Describe Types of Data Processing and Storage Systems * Explain How Data Changes 3 - UNDERSTANDING TYPES AND CHARACTERISTICS OF DATA * Understand Types of Data * Break Down the Field Data Types 4 - COMPARING AND CONTRASTING DIFFERENT DATA STRUCTURES, FORMATS, AND MARKUP LANGUAGES * Differentiate between Structured Data and Unstructured Data * Recognize Different File Formats * Understand the Different Code Languages Used for Data 5 - EXPLAINING DATA INTEGRATION AND COLLECTION METHODS * Understand the Processes of Extracting, Transforming, and Loading Data * Explain API/Web Scraping and Other Collection Methods * Collect and Use Public and Publicly-Available Data * Use and Collect Survey Data 6 - IDENTIFYING COMMON REASONS FOR CLEANSING AND PROFILING DATA * Learn to Profile Data * Address Redundant, Duplicated, and Unnecessary Data * Work with Missing Value * Address Invalid Data * Convert Data to Meet Specifications 7 - EXECUTING DIFFERENT DATA MANIPULATION TECHNIQUES * Manipulate Field Data and Create Variables * Transpose and Append Data * Query Data 8 - EXPLAINING COMMON TECHNIQUES FOR DATA MANIPULATION AND OPTIMIZATION * Use Functions to Manipulate Data * Use Common Techniques for Query Optimization 9 - APPLYING DESCRIPTIVE STATISTICAL METHODS * Use Measures of Central Tendency * Use Measures of Dispersion * Use Frequency and Percentages 10 - DESCRIBING KEY ANALYSIS TECHNIQUES * Get Started with Analysis * Recognize Types of Analysis 11 - UNDERSTANDING THE USE OF DIFFERENT STATISTICAL METHODS * Understand the Importance of Statistical Tests * Break Down the Hypothesis Test * Understand Tests and Methods to Determine Relationships Between Variables 12 - USING THE APPROPRIATE TYPE OF VISUALIZATION * Use Basic Visuals * Build Advanced Visuals * Build Maps with Geographical Data * Use Visuals to Tell a Story 13 - EXPRESSING BUSINESS REQUIREMENTS IN A REPORT FORMAT * Consider Audience Needs When Developing a Report * Describe Data Source Considerations For Reporting * Describe Considerations for Delivering Reports and Dashboards * Develop Reports or Dashboards * Understand Ways to Sort and Filter Data 14 - DESIGNING COMPONENTS FOR REPORTS AND DASHBOARDS * Design Elements for Reports and Dashboards * Utilize Standard Elements * Creating a Narrative and Other Written Elements * Understand Deployment Considerations 15 - UNDERSTAND DEPLOYMENT CONSIDERATIONS * Understand How Updates and Timing Affect Reporting * Differentiate Between Types of Reports 16 - SUMMARIZING THE IMPORTANCE OF DATA GOVERNANCE * Define Data Governance * Understand Access Requirements and Policies * Understand Security Requirements * Understand Entity Relationship Requirements 17 - APPLYING QUALITY CONTROL TO DATA * Describe Characteristics, Rules, and Metrics of Data Quality * Identify Reasons to Quality Check Data and Methods of Data Validation 18 - EXPLAINING MASTER DATA MANAGEMENT CONCEPTS * Explain the Basics of Master Data Management * Describe Master Data Management Processes ADDITIONAL COURSE DETAILS: Nexus Humans CompTIA Data Plus (DA0-001) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CompTIA Data Plus (DA0-001) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

CompTIA Cloud+
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for IT professionals who wish to develop cloud computing skills to enable them to move IT workloads to the cloud and integrate products and services from different providers and industries. Their focus is to ensure that cloud deployments are secure, that automation and orchestration are used effectively to bring business value from the cloud, and that costs are controlled through effective management of cloud vendors. This course is also designed for students who are preparing to take the CompTIA Cloud+ certification exam CV0-003, or who plan to use Cloud+ as the foundation for more advanced cloud certifications or career roles. Overview In this course, you will deploy, test, secure, manage, optimize, and troubleshoot a cloud solution. You will: - Prepare to deploy cloud solutions - Deploy a pilot project - Test a pilot project deployment - Design a secure network for cloud deployment - Determine CPU and memory sizing for cloud deployments - Determine storage requirements for cloud deployments - Plan Identity and Access Management for cloud deployments - Analyze workload characteristics to ensure successful migration to the cloud - Secure systems to meet access requirements - Maintain cloud systems - Implement backup, restore, and business continuity measures - Analyze cloud systems for required performance - Analyze cloud systems for anomalies and growth forecasting - Troubleshoot deployment, capacity, automation, and orchestration issues - Troubleshoot connectivity issues - Troubleshoot security issues In this course, you will learn how to implement, maintain, and deliver cloud technologies including network, storage, and virtualization technologies to create cloud solutions. 1 - PREPARING TO DEPLOY CLOUD SOLUTIONS * Describe Interaction of Cloud Components and Services * Describe Interaction of Non-cloud Components and Services * Evaluate Existing Components and Services for Cloud Deployment * Evaluate Automation and Orchestration Options * Prepare for Cloud Deployment 2 - DEPLOYING A PILOT PROJECT * Manage Change in a Pilot Project * Execute Cloud Deployment Workflow * Complete Post-Deployment Configuration 3 - TESTING PILOT PROJECT DEPLOYMENTS * Identify Cloud Service Components for Testing * Test for High Availability and Accessibility * Perform Deployment Load Testing * Analyze Test Results 4 - DESIGNING A SECURE AND COMPLIANT CLOUD INFRASTRUCTURE * Design Cloud Infrastructure for Security * Determine Organizational Compliance Needs 5 - DESIGNING AND IMPLEMENTING A SECURE CLOUD ENVIRONMENT * Design Virtual Network for Cloud Deployment * Determine Network Access Requirements * Secure Networks for Cloud Interaction * Manage Cloud Component Security * Implement Security Technologies 6 - PLANNING IDENTITY AND ACCESS MANAGEMENT FOR CLOUD DEPLOYMENTS * Determine Identity Management and Authentication Technologies * Plan Account Management Policies for the Network and Systems * Control Access to Cloud Objects * Provision Accounts 7 - DETERMINING CPU AND MEMORY SIZING FOR CLOUD DEPLOYMENTS * Determine CPU Size for Cloud Deployment * Determine Memory Size for Cloud Deployment 8 - DETERMINING STORAGE REQUIREMENTS FOR CLOUD DEPLOYMENTS * Determine Storage Technology Requirements * Select Storage Options for Deployment * Determine Storage Access and Provisioning Requirements * Determine Storage Security Options 9 - ANALYZING WORKLOAD CHARACTERISTICS TO ENSURE SUCCESSFUL MIGRATION * Determine the Type of Cloud Deployment to Perform * Manage Virtual Machine and Container Migration * Manage Network, Storage, and Data Migration 10 - MAINTAINING CLOUD SYSTEMS * Patch Cloud Systems * Design and Implement Automation and Orchestration for Maintenance 11 - IMPLEMENTING BACKUP, RESTORE, DISASTER RECOVERY, AND BUSINESS CONTINUITY MEASURES * Back Up and Restore Cloud Data * Implement Disaster Recovery Plans * Implement Business Continuity Plans 12 - ANALYZING CLOUD SYSTEMS FOR PERFORMANCE * Monitor Cloud Systems to Measure Performance * Optimize Cloud Systems to Meet Performance Criteria 13 - ANALYZING CLOUD SYSTEMS FOR ANOMALIES AND GROWTH FORECASTING * Monitor for Anomalies and Resource Needs * Plan for Capacity * Create Reports on Cloud System Metrics 14 - TROUBLESHOOTING DEPLOYMENT, CAPACITY, AUTOMATION, AND ORCHESTRATION ISSUES * Troubleshoot Deployment Issues * Troubleshoot Capacity Issues * Troubleshoot Automation and Orchestration Issues 15 - TROUBLESHOOTING CONNECTIVITY ISSUES * Identify Connectivity Issues * Troubleshoot Connectivity Issues 16 - TROUBLESHOOTING SECURITY ISSUES * Troubleshoot Identity and Access Issues * Troubleshoot Attacks * Troubleshoot Other Security Issues ADDITIONAL COURSE DETAILS: Nexus Humans CompTIA Cloud Plus Certification (Exam CV0-003) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CompTIA Cloud Plus Certification (Exam CV0-003) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Becoming a Transformational Leader
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Managers, directors, executives, and others responsible for leading teams, overseeing projects, and developing new leaders will benefit from this course. Overview Bring about valuable and positive change in those you lead Increase engagement, motivation and morale in your team Enhance performance of individuals and the team Provide an authentic role model that inspires followership Develop others into leaders This course will help students develop authentic leadership qualities that motivate and drive others to reach their full potential, and become the transformational leaders of the future. Private classes on this topic are available. We can address your organization?s issues, time constraints, and save you money, too. Contact us to find out how. 1. DEFINING TRANSFORMATIONAL LEADERSHIP * Comparing Leadership Styles * Developing the Attitudes and Beliefs of a Transformational Leader 2. BEING AN AUTHENTIC LEADER * Knowing Who You Are * Fostering Authenticity and Credibility 3. DEMONSTRATING LEADERSHIP PRACTICE * Following the Five Practices of Exemplary Leadership 4. BUILDING ENGAGEMENT AND MOTIVATION * Understanding the Drivers of Employee Engagement * Motivating Like a Transformational Leader 5. OPTIMIZING PERFORMANCE * Coaching for Performance * Supporting Performance through Partnership * Unlocking Potential * Developing and Transforming Careers 6. MENTORING LEADERS * Growing Leaders * Putting Relationships First * Focusing on Character * Capitalizing on Strengths * Showing Optimism and Not Skepticism * Seeking Passion and Success 7. COMMITTING TO TRANSFORMATIONAL LEADERSHIP

Character Animation in 3ds Max Training
By London Design Training Courses
Why Choose Character Animation in 3ds Max Training Course? Click here for more info. [https://www.londondesigntrainingcourse.co.uk/product-page/character-animation-in-3ds-max-training-course] Top character animation course in 3ds Max, this course provides an accessible learning experience. Learning character animation enables you to create your own short films. It's not just a means of income; it evolves into a passion. Duration: 20 hrs Method: 1-on-1, Personalized attention. Schedule: Tailor your own hours of your choice, available from Monday to Saturday between 9 am and 7 pm. Enroll in our exclusive "Character Animation Fundamentals in 3ds Max" course at London Design Training, guided by experienced tutors Sitwat Ali, Qasim Ali, and Jess. Gain in-depth insights into animating 3D characters, covering essential techniques like character rigging, pose creation, and seamless pose-to-pose animation. 3ds Max Character Animation Course Duration: 20 hours Course Overview: Master the art of character animation in 3ds Max with our comprehensive course. Ideal for beginners and those with some 3D modeling and animation experience, this course covers everything you need to know to bring characters to life. Course Outline: * Introduction to Character Animation * Explore animation principles * Get familiar with 3ds Max animation tools * Learn to create character rigs and manage the timeline * Basic Animation Principles * Understand keyframes and animation cycles * Apply the 12 principles of animation * Work with the graph editor and ease-in/out techniques * Advanced Animation Techniques * Utilize the reaction manager for complex animations * Master non-linear animation methods * Animate with inverse kinematics, custom controllers, expressions, and scripts * Creating Characters * Craft a character model with proper topology * Create UV maps and apply textures * Prepare characters for rigging * Facial Animation * Learn facial animation principles * Create blend shapes and morph targets * Master lip syncing techniques * Body Animation * Animate walk cycles and character motion * Achieve believable character poses * Implement character physics * Advanced Character Animation * Work with motion capture data * Use CAT and Biped tools * Understand motion blur and create special effects * Render and output animations * Character Animation Projects * Bring all skills together in practical projects * Create basic and complex character animations Course Requirements: * Computer with 3ds Max installed * Basic computer operations knowledge * Passion for character animation Course Goals: Upon completion, you'll have a thorough grasp of character animation in 3ds Max, capable of creating realistic and sophisticated character animations using advanced techniques. You'll be equipped with the skills to continue honing your character animation abilities independently.
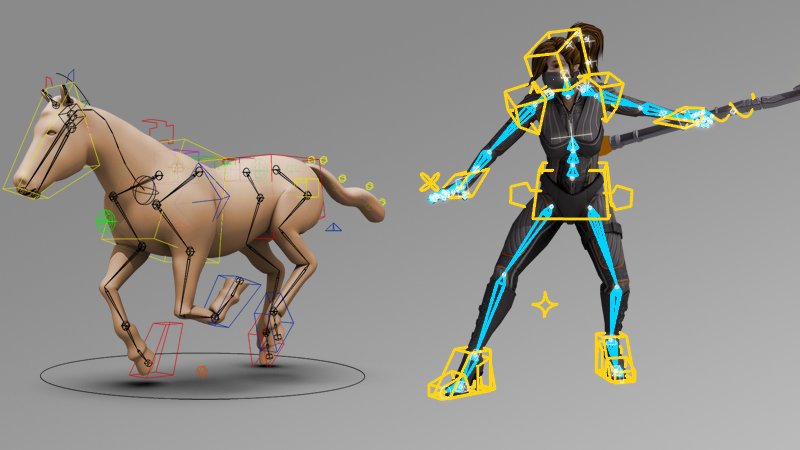
Blender 3D - Learn Character Modelling
By Course Gate
Learn the fundamentals of Blender software, explore techniques for creating detailed 3D models, and master the process of rendering your creations. Whether you're a beginner or an experienced designer, this course will equip you with the skills needed to bring your characters to life in the digital world.

Create A Character From The Post-Apocalypse
By Course Cloud
COURSE OVERVIEW Make a dynamic image of a fictional figure from a far-off future by taking this course on how to Create a Character from The Post-Apocalypse. Exploring the years ahead of humanity has never been more popular in the media and provides plenty of artistic potentials. This tutorial will guide you in visually conceptualising a resident from a distant possible reality. By taking this Character Creation coaching, you can follow the steps to produce a drawing of a fictional figure that might be able to survive and thrive in any circumstance. From blank paper to the final image, you will be guided in seeking inspiration and bringing your ideas to the page. By creating this character and producing an eye-catching image, you will learn how to populate a post-apocalypse world with more of your creations. This best selling Create A Character From The Post-Apocalypse has been developed by industry professionals and has already been completed by hundreds of satisfied students. This in-depth Create A Character From The Post-Apocalypse is suitable for anyone who wants to build their professional skill set and improve their expert knowledge. The Create A Character From The Post-Apocalypse is CPD-accredited, so you can be confident you're completing a quality training course will boost your CV and enhance your career potential. The Create A Character From The Post-Apocalypse is made up of several information-packed modules which break down each topic into bite-sized chunks to ensure you understand and retain everything you learn. After successfully completing the Create A Character From The Post-Apocalypse, you will be awarded a certificate of completion as proof of your new skills. If you are looking to pursue a new career and want to build your professional skills to excel in your chosen field, the certificate of completion from the Create A Character From The Post-Apocalypse will help you stand out from the crowd. You can also validate your certification on our website. We know that you are busy and that time is precious, so we have designed the Create A Character From The Post-Apocalypse to be completed at your own pace, whether that's part-time or full-time. Get full course access upon registration and access the course materials from anywhere in the world, at any time, from any internet-enabled device. Our experienced tutors are here to support you through the entire learning process and answer any queries you may have via email.
