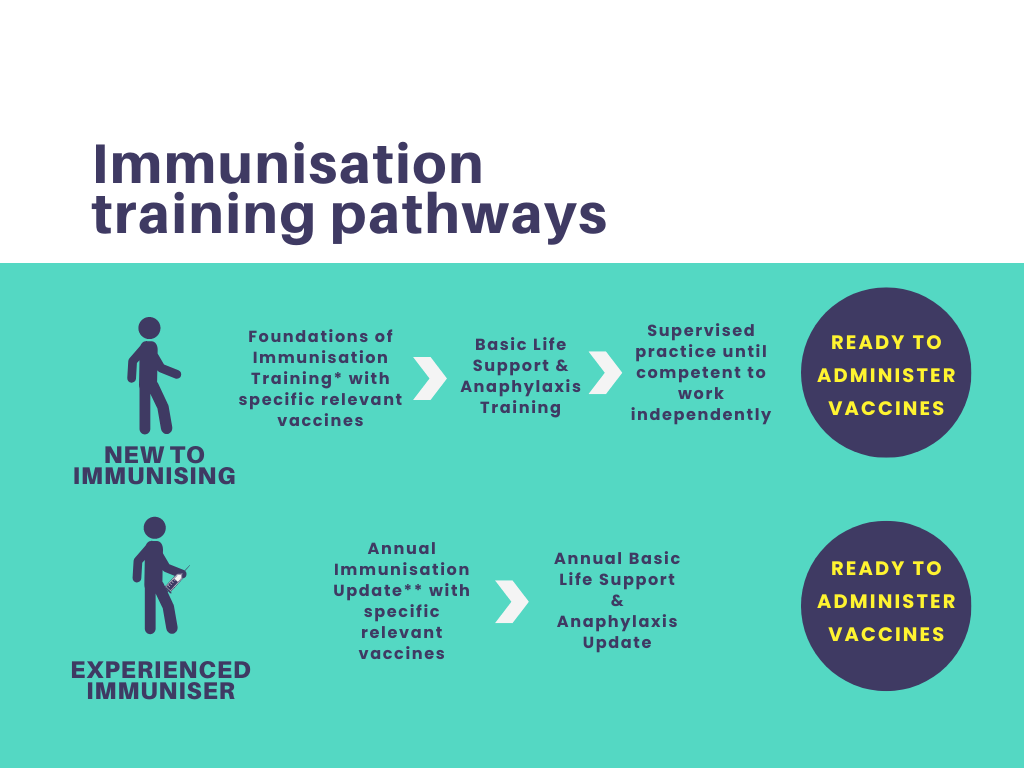
Foundations of Immunisation and Vaccines
By Guardian Angels Training
Gain a comprehensive understanding of immunisation and vaccines with our "Foundations of Immunisation and Vaccines" course. Designed for healthcare professionals, public health workers, and individuals interested in immunisation, this course covers vaccine development, administration, safety, and the role of vaccines in preventing infectious diseases.
OVERVIEW -------------------------------------------------------------------------------- This course will take you through learning how and when a contract is formed, analysing various terms in the contract, identifying various factors that can quash the contract and ways to discharge the contract also ways to protect the company if there is a breach of contract.

OVERVIEW -------------------------------------------------------------------------------- The effective management of finances is a fundamental function for any organisation but particularly so in the public sector. Governments, under the scrutiny of the citizens they represent, are increasingly under pressure to improve public services whilst at the same time identifying ways to cut spending and increase efficiency. This programme recognises these difficulties and ensures that participants leave the programme with a full understanding of effective financial management in the public sector - including budgeting systems, auditing, preparing financial statements and tracking expenditure.

MICROSOFT LYNC TRAINING COURSE DESCRIPTION This course teaches IT staff how to plan, design, deploy, configure, and administer a Microsoft Lync Server solution. The course emphasizes Lync Server Enterprise Unified Communications features focussing particularly on coexisting with and migrating from legacy communication services. The labs in this course create a solution that includes IM and Presence, Conferencing, and Persistent Chat. This course helps prepare for Exam 70-336. WHAT WILL YOU LEARN * Describe the Lync Server architecture. * Install and deploy Lync Server. * Use Lync Server management interfaces. * Deploy and manage clients. * Manage and administer dial-in conferencing. * Design audio and video for web conferencing. * Plan for instant message and presence Federation. * Deploy and configure persistent chat in Lync. * Configure archiving and monitoring services. * Troubleshoot Lync Server. * Describe the required daily, weekly, and monthly maintenance tasks. * Use SIP commands and analyze SIP logs. * Configure high availability features in Lync. * Design load balancing in Lync Server. * Backup and restore Lync Server data. MICROSOFT LYNC TRAINING COURSE DETAILS * Who will benefit: Technical staff working with Microsoft Lync. * Prerequisites: Supporting Windows 2008 or 2012. * Duration 5 days MICROSOFT LYNC TRAINING COURSE CONTENTS * Microsoft Lync Server architecture Lync Server architecture, Lync core capabilities, Lync design process, assessing infrastructure requirements and updating the design, planning for all Microsoft solutions framework phases. * Designing a Lync Server topology Infrastructure requirements for Lync Server, using the planning tool, using topology builder, server infrastructure, documentation. Hands on Environment preparation and Lync Server pools. * Users and rights in Microsoft Lync Server Managing Lync Server, role based access control. Hands on Using the management shell, configuring role-based access control. * Client/device deployment and management Deploy and manage clients, prepare for device deployment, IP phones. Hands on Clients. * Conferencing in Lync Server Introduction to conferencing in Lync Server, designing for audio\video and web conferencing, dial-in conferencing in Lync Server, managing and administering conferencing. Hands on Conferencing in Microsoft Lync. * Designing and deploying external access Conferencing and external capabilities of Lync Server, planning for IM and presence federation, designing edge services. Hands on Deploying Edge Server and Configuring Remote Access, Validating the Edge Server. * Deploying Lync Server persistent chat Overview of persistent chat architecture in Lync Server, designing persistent chat, deploying and persistent chat. Hands on persistent chat server. * Monitoring and archiving The archiving service, the monitoring service, configuring archiving and monitoring. Hands on Archiving and monitoring in Lync Server. * Administration and maintenance of Lync Lync Server troubleshooting tools, Lync Server operational tasks, Lync Server troubleshooting techniques. Hands on Lync administration tools, centralized logging service, analysing Lync Server logs and traces. * High Availability in Lync Server High availability in Lync Server, configuring high availability in Lync Server, planning for load balancing, designing load balancing. Hands on Configuring database mirroring, experiencing a scheduled SQL Server outage, experiencing an unscheduled SQL Server outage. * Disaster recovery in Lync Server Disaster recovery in Lync Server, tools for backing up and restoring Lync Server, critical Lync Server data to back up and restore, critical data to export and import, designing branch site resiliency. Hands on Configure pool pairing, experiencing a pool failure or outage. * Planning a migration to Lync Server Coexistence and migration, migration steps, planning for clients and devices. Designing a client migration and device migration strategy. Hands on Creating a migration plan, documenting the migration phases.

How to identify and mitigate procurement fraud and corruption - IN PERSON
By Global Risk Alliance Ltd
Our training programme will provide those involved at any stage of the process for procuring goods and/or services within their organisations with the knowledge and skillset to identify and mitigate the threat posed by the breadth and multi-layered complexity of procurement fraud and corruption.

ADVANCED JUNOS SECURITY TRAINING COURSE DESCRIPTION This course provides students with intermediate routing knowledge and configuration examples. The course includes an overview of protocol-independent routing features, load balancing and filter-based forwarding, OSPF, BGP, IP tunneling, and high availability (HA) features. Junos Intermediate Routing (JIR) is an intermediate-level course. WHAT WILL YOU LEARN * Demonstrate the understanding of integrated user firewall. * Implement next generation Layer 2 security features. * Implement virtual routing instances in a security setting. * Utilize Junos tools for troubleshooting Junos security implementations. * Implement IPS policy. ADVANCED JUNOS SECURITY TRAINING COURSE DETAILS * Who will benefit: Individuals responsible for implementing, monitoring, and troubleshooting Junos security components. * Prerequisites: Intro to the Junos Operating System * Duration 5 days ADVANCED JUNOS SECURITY TRAINING COURSE CONTENTS * Junos Layer 2 Packet Handling and Security Features Transparent Mode Security Secure Wire Layer 2 Next Generation Ethernet Switching MACsec Lab 2 Implementing Layer 2 Security * Virtualization Virtualization Overview Routing Instances Logical Systems Lab 3 Implementing Junos Virtual Routing * AppSecure Theory AppSecure Overview AppID Overview AppID Techniques Application System Cache Custom Application Signatures * AppSecure Implementation AppTrack AppFW AppQoS APBR SSL Proxy Lab 4 Implementing AppSecure * Working with Log Director Log Director Overview Log Director Components Installing and setting up Log Director Clustering with the Log Concentrator VM Administrating Log Director Lab 5 Deploying Log Director * Sky ATP Theory Sky ATP Overview Monitoring Sky ATP Analysis and Detection of Malware * Sky ATP Implementation Configuring Sky ATP Installing Sky ATP Analysis and detection of Malware Infected Host Case Study Lab 6 Instructor Led Sky ATP Demo * Implementing UTM UTM Overview AntiSpam AntiVirus Content and Web Filtering Lab 7 Implementing UTM * Introduction to IPS IPS Overview Network Asset Protection Intrusion Attack Methods Intrusion Prevention Systems IPS Inspection Walkthrough IPS Policy and Configuration SRX IPS Requirements IPS Operation Modes Basic IPS Policy Review IPS Rulebase Operations Lab 8 Implementing Basic IPS Policy * SDSN SDSN Overview, Components & Configuration Policy Enforcer Troubleshooting SDSN Use Cases Lab 9 Implementing SDSN * Enforcement, Monitoring, and Reporting User Role Firewall and Integrated User Firewall Overview User Role Firewall Implementation Monitoring User Role Firewall Integrated User Firewall Implementation Monitoring Integrated User Firewall Lab 10 Configure User Role Firewall and Integrated User Firewall * Troubleshooting Junos Security Troubleshooting Methodology Troubleshooting Tools Identifying IPsec Issues Lab 11 Performing Security Troubleshooting Techniques * Appendix A: SRX Series Hardware and Interfaces Branch SRX Platform Overview High End SRX Platform Overview SRX Traffic Flow and Distribution SRX Interfaces

SECURING UNIX SYSTEMS TRAINING COURSE DESCRIPTION This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. WHAT WILL YOU LEARN * Secure UNIX accounts. * Secure UNIX file systems. * Secure UNIX access through the network. SECURING UNIX SYSTEMS COURSE DETAILS * Who will benefit: Linux technical staff needing to secure their systems. * Prerequisites: Linux system administration (LPIC-1) * Duration 5 days SECURING UNIX SYSTEMS COURSE CONTENTS * Cryptography * Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. * Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. * Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. * DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. * Host Security * Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. * Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. * User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. * FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. * Access Control * Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. * Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. * etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. * Network Security * Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. * Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. * Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd * Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

An Understanding of Seizure First Aid and the Administration of Rectal Paraldehyde
By Guardian Angels Training
Gain comprehensive knowledge and practical skills in seizure first aid and rectal paraldehyde administration with our course. Ideal for caregivers, healthcare professionals, educators, and individuals.

An Understanding of Seizure First Aid and Simulated Administration of Buccal Midazolam (non-RQF)
By Guardian Angels Training
Gain comprehensive knowledge and practical skills in seizure first aid and buccal midazolam administration with our non-regulated qualification course. Ideal for caregivers, educators, and family members.

An Understanding of Oxygen Administration
By Guardian Angels Training
Gain comprehensive knowledge and practical skills for safe and effective oxygen therapy with our "An Understanding of Oxygen Administration" course. Equip yourself with evidence-based best practices to assess, administer, and monitor oxygen therapy appropriately. Ideal for healthcare professionals.

Search By Location
- Admin Courses in London
- Admin Courses in Birmingham
- Admin Courses in Glasgow
- Admin Courses in Liverpool
- Admin Courses in Bristol
- Admin Courses in Manchester
- Admin Courses in Sheffield
- Admin Courses in Leeds
- Admin Courses in Edinburgh
- Admin Courses in Leicester
- Admin Courses in Coventry
- Admin Courses in Bradford
- Admin Courses in Cardiff
- Admin Courses in Belfast
- Admin Courses in Nottingham